Ensuring the ability to handle one’s own data safely is crucial and maintaining control over international transfers of that data can help with protecting sensitive information from cyberattacks traversing multiple jurisdictions.
Data sovereignty is the idea that data is subject to the laws of its country or region in which it was created.
Closely related to data residency — which is sometimes uses as a synonym for the concept, governance and security are some of considerations defining strategies in organizations that handle where they store their information or who processes/transfers it. Ensuring the ability to handle one’s own data safely is crucial and maintaining control over international transfers of that data – a concept known as ‘data sovereignty’ can help with protecting sensitive information from cyberattacks traversing multiple jurisdictions.
Data sovereignty, security and localization are all synonyms to some extent. Data Sovereignty vs Data Residency — Explanation & Overview While there can be many similarities between what organizations may require cloud computing technologies to do and fulfill as part of their digital transformation journey, they are not the same.
Data sovereignty: This means data that is stored and processed where they were produced.
Data residency: Data stored in a different country than where it was generated.
Data residency compliance: This is the complete process of adhering to all regulations and policy about where data must live.
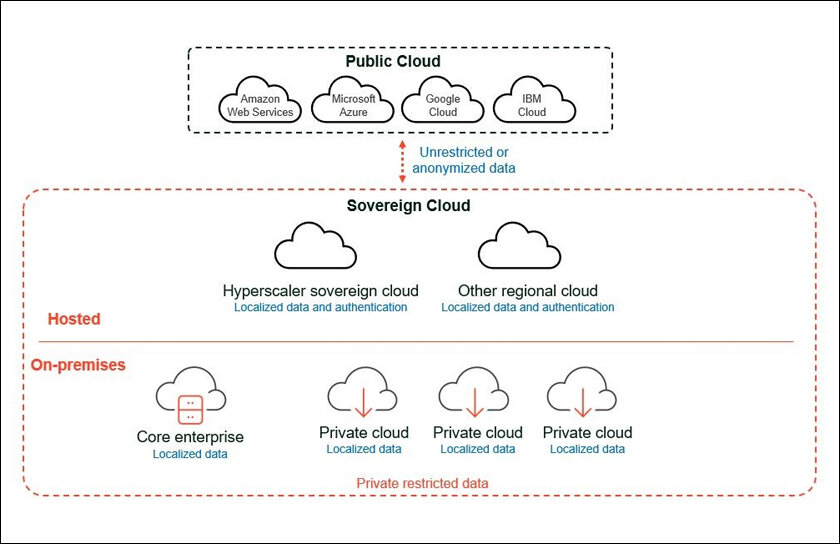
What is sovereign cloud?
Sovereign Cloud is a type of cloud computing that provides organizations with the ability to comply with specific data residency and sovereignty requirements which vary by country but typically require customer data remain in their legal boundaries Data Sovereignty, Residency and Localization are key elements of this concept.
With the growth of cloud storage adoption, borders are not enough to guard protected data. With the emergence of AI and ML-based data-intensive technologies which require immediate access to even massive sources of information, enterprises are compelled to orchestrate strategic choices around cloud security as well. AI — and especially generative AI such as GPT-3 have the power to inspire innovative business ideas, but they need a powerful cloud infrastructure that is both extremely fast and very secure.
This is what leads us to the sovereign cloud, a construct that covers data sovereignty, operational sovereignty and digital sovereignty. As per the statement by Akhil Jalagam, Sovereign Cloud Frameworks are enabling businesses to gain their customers faith and expand business across different regions with proper adherence to data collection, storage and privacy laws.
What is Data Sovereignty?
Admittedly, the need for data sovereignty arises due to its growing significance in cloud computing environments as one of many key building blocks for organizations that use various dimensions from it within their overall growth strategy.
All enterprise applications in the cloud must rely on a provider, and to that extent their health is dependent upon this critical infrastructure as any factory or office building of an earlier age.
The common reasons behind data sovereignty requirements are the laws about storing personal information in a country or region. These include typical issues core to organizations wanting to comply with local laws, including cybersecurity, data protection and privacy (keeping sensitive details of individuals private from unnecessary access), as well controlling who is enable whether they are people or entities could be able access this information.
The European Union (EU), for one, has a General Data Protection Regulation (GDPR) that necessitates companies operating inside EU territory and managing with any data regarding an EU citizen to appoint someone called the Data Protection Officer or DPO so as to verify if these businesses are thoroughly keeping data they generate, process and store confidentially intact in integrity condition fitting conformity.
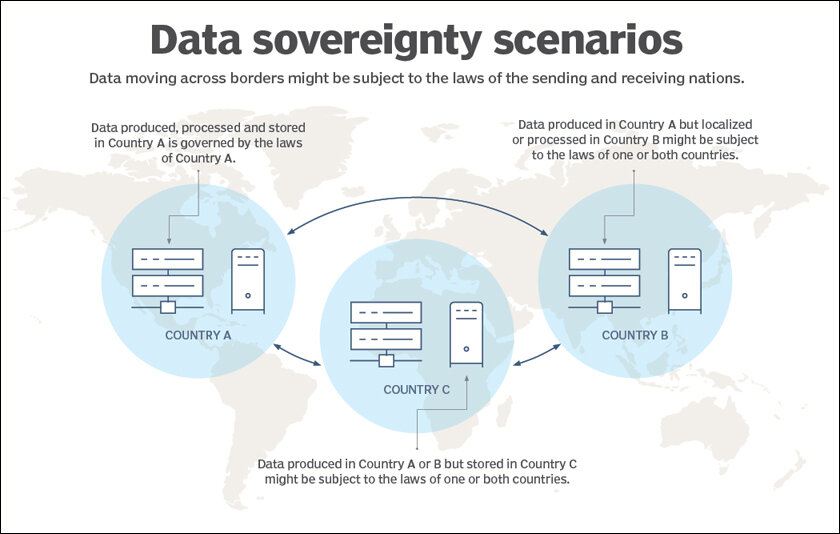
What is data sovereignty?
Data sovereignty is governed by the laws and regulations that applicable to the location, or country where data was created. The specificity of these laws differ between jurisdictions, but usually when we say that a country has the ‘‘sovereignty over’’ some piece of data; what is meant specifically is that the state presumes jurisdiction and control — later on in relation to who uses this specific bit of information or gets access to it. However, frequently the data is governed by more than just one country’s laws (data residency and ‘on premise’ or in-country processing etc.) thereby complicating how it can be handled.
Where data is created in one country or region but stored and/or processed somewhere else, the organization managing that data must comply with relevant privacy laws regarding datasets associated with all entities involved. Enterprises may have to (for instance) create DPA:s to the data protection authorities, and/or also design/develop specific protocols so that they can still operate in some territories without risking fines. If your organization is also storing or processing data in various regions/countries, you might want to consider looking into the necessary data protection laws (or cross-border restrictions) and related issues that need to be considered for information integrity.
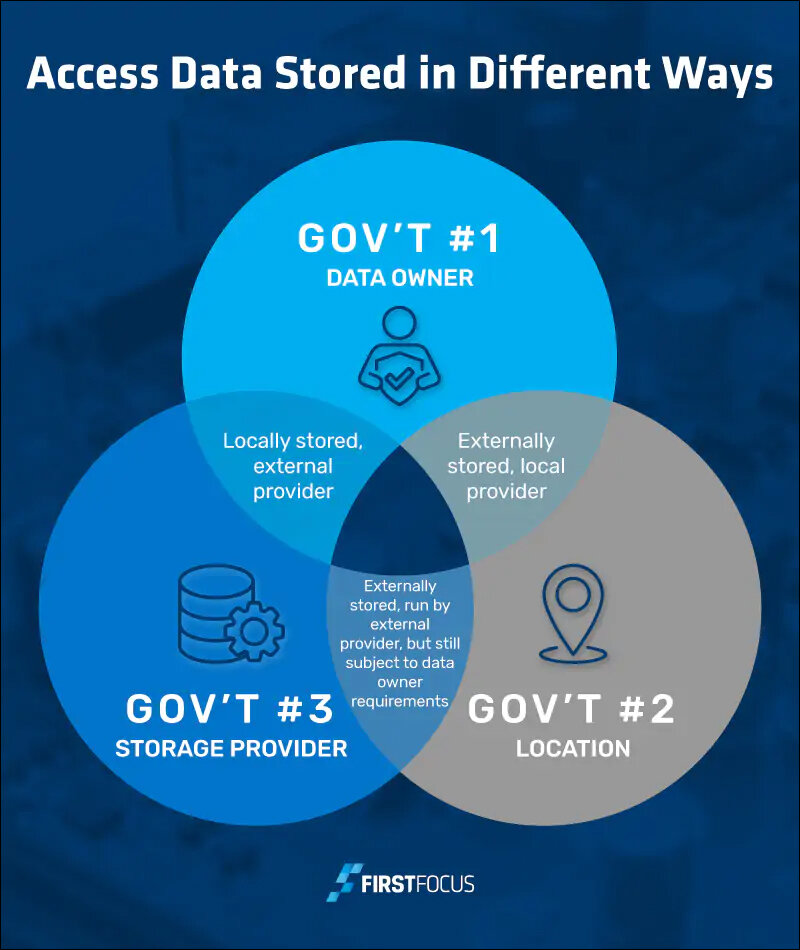
Data sovereignty: How it works?
In addition, for an organization to be successful with its data sovereignty approach, two more equally important components are required: operational and digital Sovereignty. Data, operational and digital sovereignty are the three key components of sovereign cloud infrastructure. Operational sovereignty (Critical Infrastructure is always available to individuals, entities and application) Digital Sovereignty (An organization controls access to its digital assets at all times.) Read on to learn more about each one and why you should care.
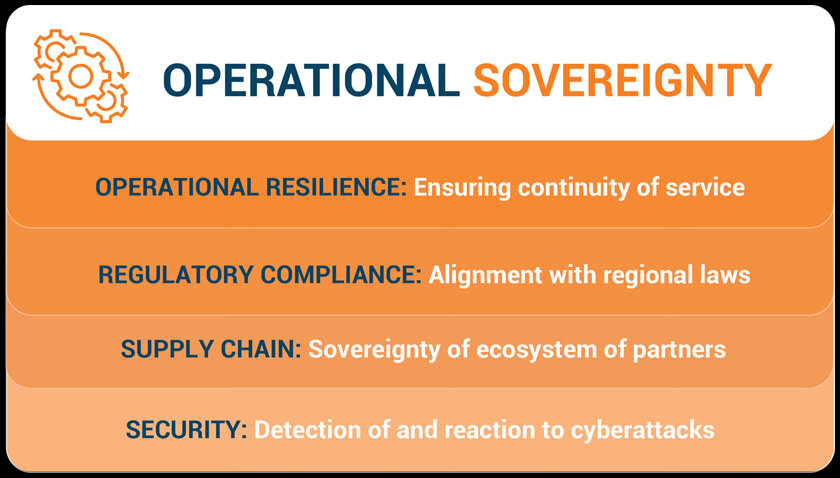
Operational sovereignty
Operational sovereignty guarantees that mission-critical structures of data-rich applications are maintained up-and-running and can be approached. And operational sovereignty provided by enterprises, ensures transparent and controlled operational processes so as to identify inefficiencies.
By operating under a premise of rational operational sovereignty, an enterprise can maintain its critical infrastructure across the world and guarantee it is closer to disaster not just in time but operationally too. One way to accomplish this is for many operational sovereignty approaches will include a business continuity disaster recovery (BCDR) or more aptly, in my opinion at least )disaster Recovery as service plan. And, operational sovereignty gives enterprises that are subject to local regulations around the infrastructure required to house public cloud environments in a region.
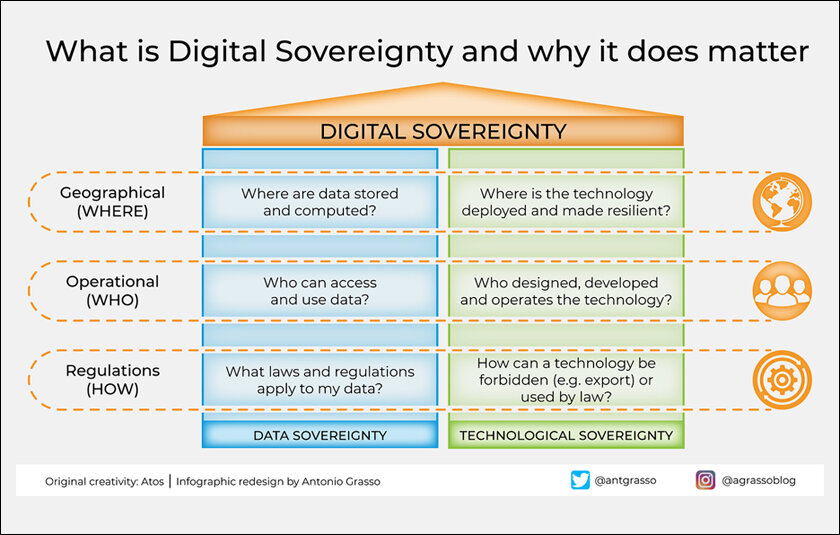
Digital sovereignty
It is most commonly used in the context of an organization and generally refers to how much control said organization has over its digital assets, such as data, software or content, or other relevant parts of the so called “digital infrastructure. With the concept of sovereign cloud, digital sovereignty is crucial when it comes to governance and transparency. These companies controlling ownership of the intangible property must establish terms related to who may gain access and permissions, as well as those that are under specific constraints. So, the challenge here is setting those rules in a way that you can enforce them, which takes us back to policy-as code where allows an organization to manage their infrastructure and procedures as repeatable version.
Another major digital sovereignty criterion is transparency which means that an organization should be able to audit its processes and results. Transparency lets an organization see into their critical business workflows (revenue generation, customer onboarding, operations) to understand what is and isn’t working.
Watch out for our next publish on the same content to know more about the cloud models, 3 step approach on data sovereignty and Key facts for organizations looking to start data sovereignty.









