The future of cyber security is not about developing higher barriers but about smart defence and early warning systems.
Cybersecurity is far from being an IT issue; it is a business issue for companies operating today in the digital environment. The year 2024 is still uncertain, and going further through social networks, one can see that cyber threats are developing at a rather incredible speed. As pointed out in a Cybersecurity Ventures report, cybercrime is anticipated to cost the whole world $10.5 trillion annually by the year 2025. This fact shows that businesses must act more efficiently by strengthening their defences.
Let us assume a situation whereby attackers compromise a large online retail store and get access to millions of consumer credit card details. The financial implications for the company would be costly, but that is not all that will suffer a complete disaster. Loss of customer confidence and legal consequences can directly affect the company at its core. This is just one case that shows how much a cyber attack can ruin a business.
The upshot yet again is that there are preventive measures that companies can consider as a protective measure against these risks. Organisations can fortify themselves against cyber threats by adopting appropriate security measures and receiving regular updates on the latest risks in the cybersecurity landscape. Here, you will discover 5 key trends that are defining the cybersecurity landscape in 2024 to assist you in protecting your business in an increasingly digitalized environment.
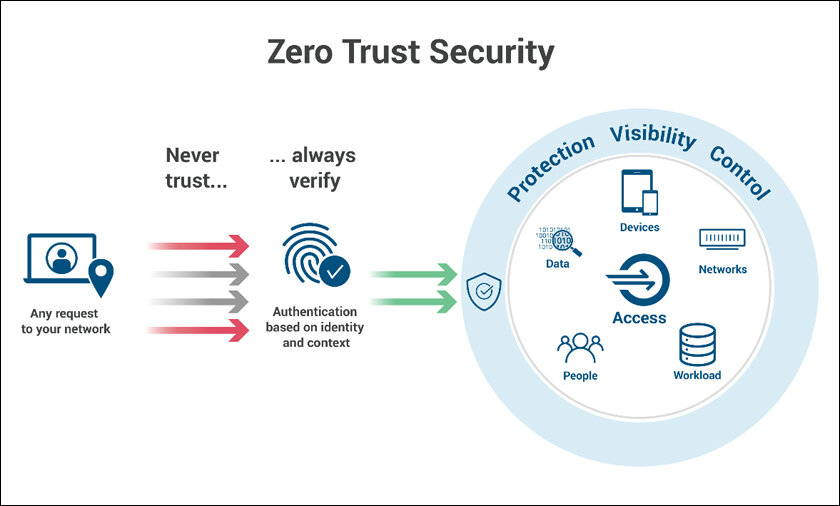
Zero Trust Architecture: A Need, Not an Option
Assuming that everyone in a circle or network is harmless is no longer safe. Zero Trust is a security framework that does not trust anyone, including employees, but instead verifies them. All individuals should be kept honest at all times and only have access to the right data they need for their job. Try to imagine it as a sort of security complex where all individuals need a certain type of key “to get through to certain zones.” ‘Zero Trust is a paradigm shift,’ according to Niall Browne, CISO of cybersecurity firm Palo Alto Networks. This scenario is described as shifting from the presumption of trust to a model that requires constant attestation of trust. Here’s how to put Zero Trust into action: For the ZTA, businesses should subdivide their networks and create smaller perimeters to achieve the goal, require all users to use multi-factor authentication (MFA), and always analyze traffic flow for signs of intrusion. Effective solutions may use Palo Alto Networks for zero-trust solutions, Okta for identity and access management, and Splunk for continuous monitoring. Other options include, for instance, utilizing Cloud Access Security Brokers (CASBs) to address the issues of access to cloud resources.
AI and Machine Learning: Improving Threat Recognition
Remember the strings of distorted letters you had to type to show you were a human and not an automated bot (CAPTCHAs)? Well, AI is getting so smart that it can often bypass them. But here’s the good news: AI can also be a great ally when it comes to maintaining your cybersecurity strategies. Imagine having a watchdog who never sleeps and can spot even the most cunning hacker lurking in the darkness of the web. Security professionals foresee that with the growing use of artificial intelligence, threat detection systems will help mitigate about 30% of cyberattacks by 2025. How does it work? AI can process large amounts of input data quicker than traditional computing methods and can detect abnormal activities and potential cybercrimes before they occur. However, you can take advantage of it by using artificial intelligence-based security information and event management (SIEM) systems, which capture data from your entire network and look for signs of suspicious activity as well as initiate an appropriate response. Also, businesses can purchase solutions such as Darktrace or Cylance, which are based on ML algorithms that analyze past data and reveal potential cyber threats, ensuring respective AI models are updated periodically to address new threats. Some technologies include Darktrace for threat visualizations, Cylance for proactive endpoint security, and IBM Watson for superintelligence.
Rise of Ransomware-as-a-Service (RaaS): An Emerging Menace
The term “ransomware-as-a-service” describes business models in which creators of ransomware lease their software to affiliated companies, enabling less technically proficient criminals to use ransomware. This enhances the regularity and complexity of such attacks, which are potentially dangerous to businesses of all sorts. The economic impact of a ransomware attack is not just about the money demanded to unlock the systems but also the financial loss incurred due to system downtime and data loss. With the help of ransomware-as-a-service, cybercriminals have opened the door to all those willing to enter the business and become a threat; hence, this is one of the biggest threats companies and organizations encounter nowadays. Defensively, organizations should create data backups that should not be connected to the internet, conduct anti-phishing and general security awareness campaigns among their employees, and incorporate strong endpoint protection solutions. Some of the best modern technologies include Veeam for backup and recovery, KnowBe4 for security awareness training, and Symantec Endpoint Protection.
Cloud Security: Securing the Bytes
As it remains evident, with many organizations shifting their operations online, safeguarding these domains is critical. The term “cloud security” describes the safeguards implemented to guarantee the safety of cloud data, cloud-based applications, and cloud infrastructure Some of the major considerations are data privacy and legal compliance, identity and access management on such a decentralized platform and protection from data theft and cyber threats. Werner Vogles, CTO of Amazon, has claimed that confidentiality is not only a technology problem but also a problem of process and people. Some of the important measures to ensure cloud security are encryption for data in transit and data at rest, identity and access management controls, and continuous reviewing of cloud environments for risks. The recommended technologies include AWS Key Management Service (KMS) as a secure way of managing the key, identity and access management through Okta, and continuous security management through Azure Security Center.
Shift in attention over cyber security rules and laws
Due to the rising incidents of cyber threats, Governments globally are implementing even stronger cybersecurity measures for data security and organizational continuity. Staying in compliance with these regulations is not only necessary from a legal standpoint but is highly recommended to protect business operations. Sanctions for non-compliance include significant penalties such as fines, potential legal ramifications and negative brand image. Compliance with cybersecurity standards is another factor that contributes to positive interactions between companies, customers and partners. According to Sheryl Sandberg, Meta’s Chief Operating Officer, compliance is not merely keeping away from penalties but it is actually safeguarding your company and everybody who relies on it. To facilitate compliance, businesses must understand the cybersecurity regulations applicable to their industry, conduct security assessments and audits, and implement a cybersecurity policy. Auxiliary instruments such as the Nessus for vulnerability assessment, Qualys for security and risk assessment, and the NIST Cybersecurity Framework for the creation of effective cybersecurity measures and organizational strategies are helpful.
In conclusion
This constantly changing threat environment can all seem a little overwhelming but the good news is that the business of combating these threats is not alone. The trends for cybersecurity 2024 offer a view to the future, have a broad base, and executive many efficient methods. From the AI guardian that never sleeps to the security of the walls of a Zero Trust network, these innovations allow corporations to transition from risks waiting to happen in strongholds to advanced strongholds. The future of cyber security is not about developing higher barriers but about smart defence and early warning systems. By following these trends, several organizations provide cyber security for themselves and can also win the race by getting one step ahead of their competitors in today’s world, where everything is going digital.
In case you missed:
- Vulnerability Assessment vs Penetration Testing: Choosing the Right Strategy in 2024
- Hybrid and Multi-Cloud technologies in 2024: Developments, challenges, and Innovations
- Kickstarting your MLOps journey in 2024: Essential practices and strategies
- The Rise of FinOps and GreenOps
- Blackwell chip: Nvidia engine for breakthrough AI
- Deciphering RHEL AI: An Open Source Approach to Artificial Intelligence
- What’s new in Azure app service at Build 2024: Key announcements and features
- Forecasting the Future: Generative AI in Software Testing for 2024
- Unleashing the Power of Voice: Exploring Meta Voicebox AI
- Identifying the Best Development Tunnelling Tool: Ngrok vs. Localtunnel









