Stay ahead of emerging cyber threats in cloud environments. Ensure the integrity of your cloud data by adopting a multi-layered security approach.
As organizations and people gradually transfer their data to the cloud, dealing with cloud security issues has become a thing of critical importance. Several companies struggle with security challenges that cloud computing always brings, especially protecting sensitive information from cyber threats.

Understanding Cloud Security Threats
A cloud security threat is one that risks the data, applications, and services that are in the cloud. These threats may damage the security, confidentiality, availability, or integrity of the information. They can be data breaches, system vulnerabilities, identity theft, or insider threats, to name a few.
1. Data breaches
Data breaches occur when sensitive information like financial or technical data is accessed without authorization. Such incidents can have a range of consequences from loss of money to damage to the reputation of a business from data-related issues. In instances where cloud environments are used for off-premise storage and third-party management, there are higher chances of security threats if not adequately secured.
Incidents like the Capital One breach in 2019, in which a misconfigured cloud-based server resulted in the exposure of data of over 100 million victims, showcase the necessity of tight security measures in cloud environments.
2. Malware infections
The cloud is also prone to malware attacks, which can spread rapidly across networked resources. Employee awareness on phishing and other social engineering tactics and advanced detection and surveillance tools are keys to combating malicious software.
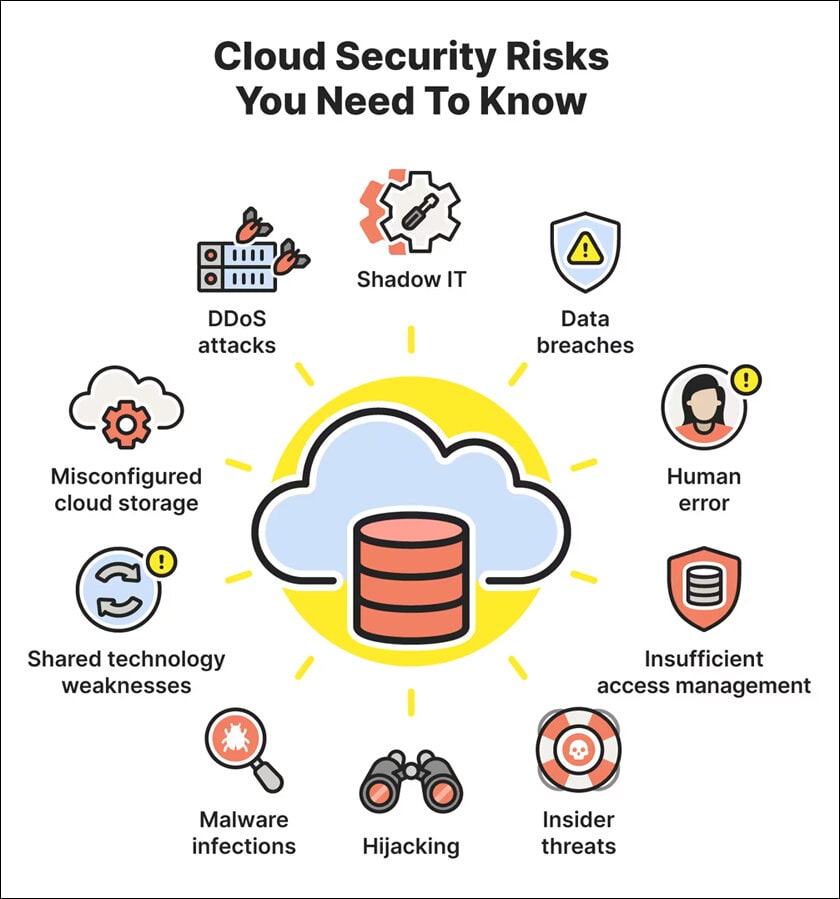
3. Distributed Denial of Service (DDoS) attacks
DDoS attacks target cloud services with enormous amounts of traffic, making it unavailable to the intended audience. Mitigating these attacks requires DDoS protection solutions that can be used to filter out the unlawful traffic.
4. Insecure APIs
Cloud services often use APIs for communication between different services. Insecure APIs can be used as a starting point for intruders, resulting in unauthorized entry and data breach.
Deploy solid authentication and authorization systems, input validation and sanitization, and API security testing and monitoring on a continuous basis to protect against these risks.
5. Misconfigured cloud services
One of the main reasons for data breaches and unauthorized access is misconfigurations of cloud services. Even the slightest of errors in configuration can cause sensitive data to be accessed by everyone.
Periodic audits and monitoring as well as the implementation of the least privilege access controls and automation of security configurations are some of the ways to mitigate this threat.

How to Combat Cloud Security Threats
1. Implement strong access control measures
Implement the principle of least privilege; grant users the minimum level of access they need for their job duties. Integrate multi-factor authentication (MFA) and audit access permissions on a regular basis.
2. Continuously monitor and analyze
Use automated security tools and services to monitor cloud environments for unauthorized access, data breaches, or any suspicious activities in real time. These help in providing real-time alerts, automated compliance checks, and insights into potential vulnerabilities.
3. Encrypt data both at rest and in transit
Encrypt all sensitive data in the cloud and the data being transferred between environments using secure protocols such as Transport Layer Security (TLS).
4. Implement regular security evaluations and penetration testing
Identify existing weaknesses and test the present security measures through regular security audits and penetration testing. Refine and strengthen security postures after the analysis.
5. Encourage a culture of awareness
Educate employees about the importance of security and phishing attacks. Create awareness of safe online conduct through regular training and seminars and sharing information on the latest cyber threats and their prevention methods.
Final Thoughts
Vigilance and proactive measures are key to guarding data from cyber threats. By recognizing the common cloud security threats and implementing strategic defenses such as strict access controls, regular security assessments, encryption, and personnel training, organizations can considerably minimize risks and safeguard data in the cloud environment.
In case you missed:
- None Found










