To protect against these attacks, organizations must take a proactive approach to managing third-party risk by implementing thorough vetting processes, monitoring continuously, segmenting access, and planning for incidents.
Third-party risk management is important due to situations such as the supply chain attacks where firms in different industries face attacks on their vulnerabilities and threats from trusted vendors or suppliers. Companies have to turn to third-party vendors for applications, infrastructures, and solutions; therefore, their attack surface increases. This paves the way for cybercriminals to penetrate even the most secure networks, thereby increasing vulnerability.
Now let’s analyze the specifics of supply chain attacks, understanding why such threats are on the rise and what measures an organization can take to recognize and counter third-party threats.
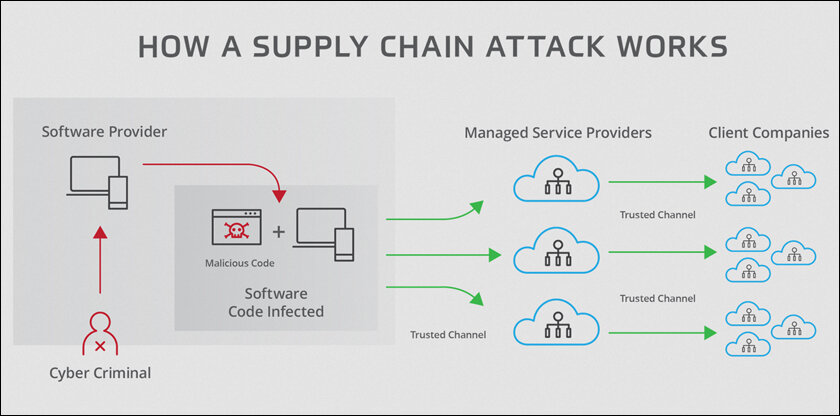
Understanding the Mechanisms of Supply Chain Attacks
Supply chain attacks happen when the vendor, supplier or third-party service provider is breached, which leads and allows attackers into the target organization. These attacks exploit the relationships and trust between organizations and third-party vendors. Once attackers get access, they can place malware, alter products, or make unauthorized use of stolen credentials to launch additional attacks or to steal data.
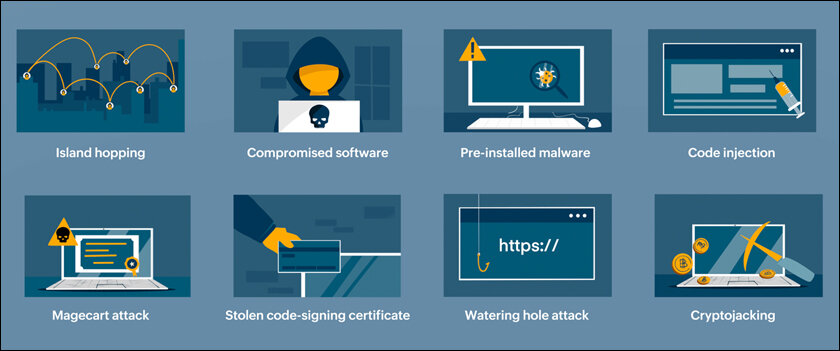
Several common methods used in supply chain attacks are as follows:
Software compromises, also known as software tampering, takes place when the attackers introduce malicious code within updates or components supplied by third parties. It can then move to a large number of organizations, as illustrated by the SolarWinds case where malicious updates were provided to customers of an IT management platform. Hardware tampering happens with products during manufacturing when malicious chips are embedded or firmware is modified. As soon as the hardware is installed in an organization’s network, the attacker has the ability to stage the attack. Credential theft is the stealing of credentials of a third-party vendor who has access to the target organization’s systems. At some point, attackers might compromise privileged accounts, or use Remote Access Tools, RATs, to move within the targeted organization’s network. Repository hijacking occurs in open-source software ecosystems where attackers can compromise the repositories, libraries or dependencies, which are used in a company’s software products. These modified components help attackers gain entry into the organization, similar to the Trojan horse.
Supply chain attacks are very dangerous due to the fact that they prey on the reliability that organizations have for their vendors; firms rely on their vendors to have adequate security practices and fail to monitor and evaluate partners. This trust, however, can turn out to be a vulnerability as adversaries mature and are better equipped for the task.
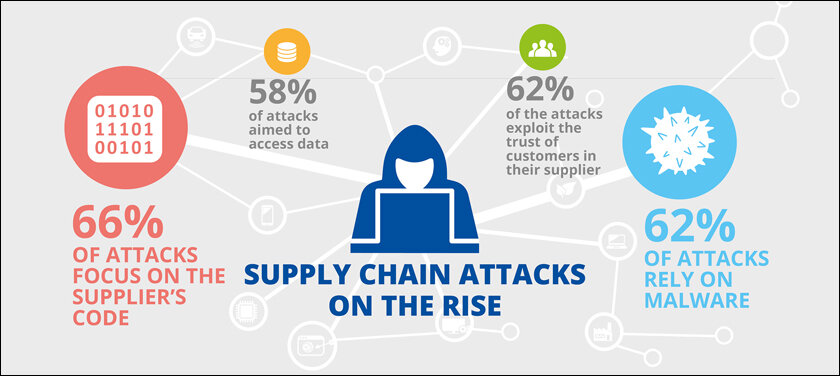
Several factors have contributed to the rise of supply chain attacks:
Supply chains are extensive, interconnected and global. Businesses depend on numerous third-party vendors; many of them have access to critical systems and data. Many of the smaller vendors require more resources to implement the same levels of cybersecurity as the big companies, and, thus, become targets for attackers. With exposures of multiple clients, third-party providers have increasingly become the target of cyber attackers.
By targeting trusted third-party vendors, cybercriminals are able to circumvent traditional defenses and gain access to their intended targets. To protect against these attacks, organizations must take a proactive approach to managing third-party risk by implementing thorough vetting processes, monitoring continuously, segmenting access, and planning for incidents.
In case you missed:
- None Found










