Implement strategies such as automated scanning, secure secrets management, and regular training.
The prediction that the DevOps market size would grow exponentially from $10.56 billion in 2023 to $12.8 billion in 2024 at a compound annual growth rate (CAGR) of 21.2% drives home the importance of securing the DevOps pipelines. These pipelines optimize the software development and deployment processes. However, they also introduce new security risks; which is why securing these pipelines becomes so important. This is to identify the vulnerabilities at an early stage.
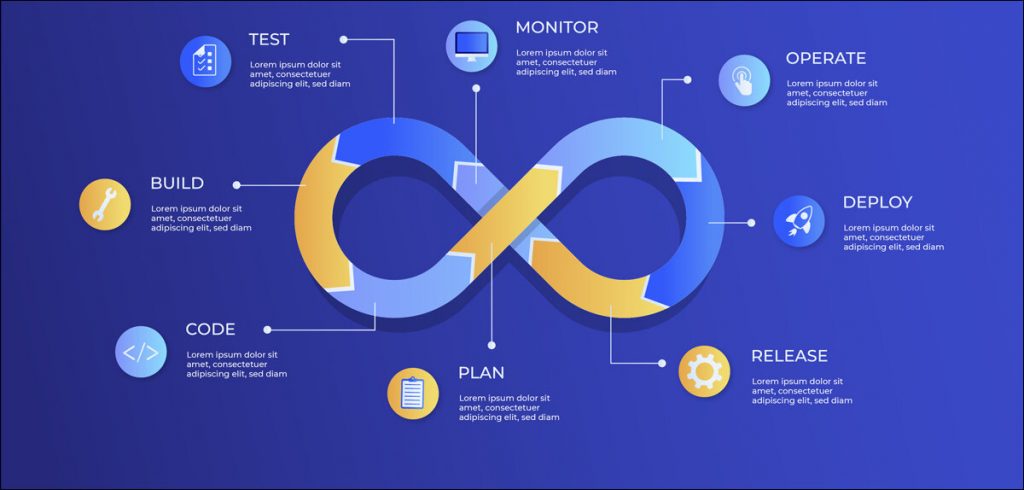
What Are DevOps Pipelines?
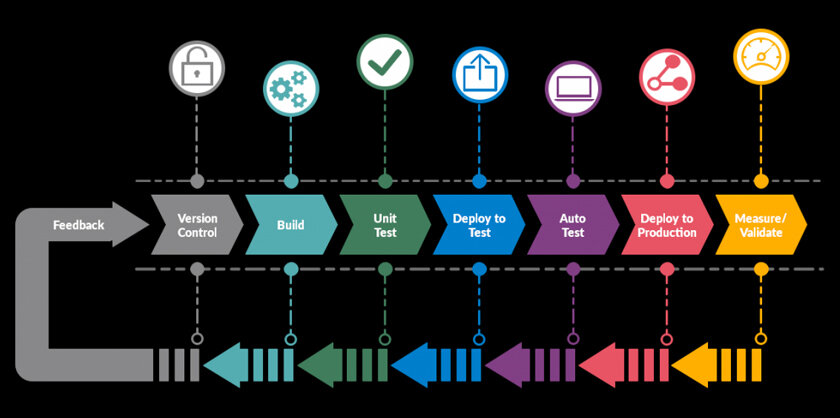
DevOps pipelines automate the development, testing, and deployment of software. There are multiple stages to the pipeline, such as code development, testing, integration, and deployment. Every stage requires various tools and processes. Although these pipelines speed up delivery, they also create potential security risks.
Why Should We Integrate Security?
Security integration in DevOps, also known as DevSecOps, is crucial. It helps in addressing security issues before production. If you don’t use it, vulnerabilities will get introduced at any stage of the pipeline and ultimately exploited. Integrating security early in the pipeline reduces risks and costs; this helps you to maintain a secure and compliant environment.

Secure your DevOps pipelines with these strategies!
1. Security from the start
Security should be a part of every stage of the pipeline. Begin with secure coding practices, ensure that all developers are aware of security guidelines, and use tools that help in detecting vulnerabilities during coding; this can prevent many issues before they escalate.
2. Security scan automation
Automated security scans are essential; they can identify vulnerabilities in code and dependencies quickly. You must include these scans in your continuous integration (CI) process and use tools that scan for known vulnerabilities in third-party libraries and components and to identify new vulnerabilities.
3. Analyzing static and dynamic applications for security
The two testing methodologies, Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), are extremely important to secure your pipeline. SAST analyzes code to detect vulnerabilities without even executing it. Whereas, DAST tests the application during runtime to find security flaws. You must deploy both of these methodologies to add 360 degree security to your DevOps pipeline.

4. Managing secrets securely
Secrets management is important in DevOps. You must store secrets like API keys and passwords very safely, use secrets management tools or vaults, avoid hardcoding secrets in code or configuration files, and regularly rotate secrets and use encryption to protect them.
5. Securing your build environment
The build environment should be safe and secure. You must ensure that your build servers and containers are protected. You should use up-to-date and secure base images for containers, regularly patch and update all components in your build environment, and monitor for any suspicious activities.
6. Enforcing access controls
Access controls help you in limiting who can have access to controls. You must use role-based access controls (RBAC) to manage permissions. You should ensure that only authorized personnel have access to crucial parts of the pipeline. You should also review and update access controls as required.

7. Deploy security training regularly
You must understand that training is the key to maintaining security. Your team members must regularly go through security training. You must ensure that everyone is aware of their role in securing the pipeline. Security drills during training help in recognizing and addressing issues effectively when they happen in real time.
8. Monitoring and logging activities
Monitoring and logging are essential for detecting and responding to threats. You must implement logging at every stage of the pipeline. Also, you must monitor for any unusual activities and analyze logs regularly to identify any security issues.
9. Integrating vulnerability management
If you do not have a proper vulnerability management plan, you cannot secure your pipelines, period! You must assess and address vulnerabilities on time. You must make use of the available tools for tracking and managing the weak spots throughout the development lifecycle. You should always consider prioritizing and fixing vulnerabilities based on their risk level.
10. Testing security regularly
Continuous testing is an important aspect of securing your DevOps pipeline. Regular security drills can help you ensure the security of your applications and infrastructure. Conducting penetration testing and security assessments and addressing any issues found during testing promptly further strengthens your pipelines.

Check out these best practices to secure your DevOps pipelines
- Shifting left: You must incorporate security early in the development process so that there are no troubles in the subsequent stages.
- Automating: You must consider automating your process for scanning and testing for efficiency.
- Collaborating: You must ensure smooth collaboration between the development, operations, and security teams. Enhancing seamless communication within your teams will help in securing your development stages.
- Keeping yourself informed: Keep yourself aware of the latest security threats and best practices. Accordingly, update your tools and processes.
Wrapping up
Securing your DevOps pipelines must be a top priority for your development environment. By leveraging the power of security methods into every stage, you can address vulnerabilities early and reduce risks. Implement strategies such as automated scanning, secure secrets management, and regular training. With these practices, you will enhance the security of your DevOps pipelines and protect your applications and data.
In case you missed:
- Zero Trust Security
- Top 5 Cloud Security Threats and How to Combat Them
- Safeguarding Remote Workforce: Data Protection Measures
- How to Implement Multi-Factor Authentication for Enhanced Security?
- Incident Response and Disaster Recovery: Preparing for the Worst-Case Scenario
- Compliance and Data Protection: Navigating Complex Regulatory Landscapes
- Common Data Protection Mistakes Businesses Must Avoid
- Data Classification and Risk Assessment: Foundations for Effective Data Protection
- Data Management Techniques
- Securing the Digital Transformation Journey: Cybersecurity Pitfalls to Avoid