With the cybersecurity landscape changing and evolving at an unimaginable pace, the enterprise attack surface is also changing continuously.
As digital ecosystems become more complex, the avenues for potential cyberattacks are also increasing greatly. Today, it is evident that companies are facing an ever-expanding attack surface, which includes various vulnerable entry points and digital assets. It is for this reason that attack surface management (ASM) has gained importance as one of the best practices for bolstering organizational defences. This security testing solution approaches security from the perspective of the attacker by continuously discovering, inventorying, classifying, and monitoring a company’s IT infrastructure. This article does a deep dive into what ASM is and why it is so important today.
What is ASM?
As mentioned above, ASM (Attack surface management) is the process of continuously identifying, prioritising, analysing, rectifying, and monitoring an enterprise’s potential attack vectors and cybersecurity vulnerabilities. ASM’s goal is to keep the attack surface minimal by reducing the number of options for hackers to breach the enterprise network perimeter.
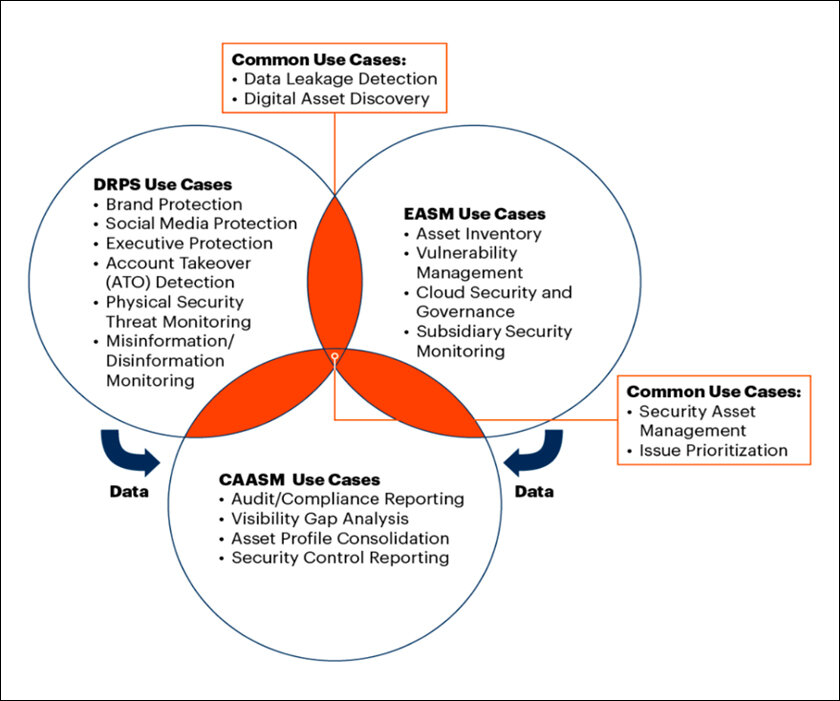
ASM activities can be divided into two broad categories:
- Managing activities on assets that are accessible from within an organization only.
- Managing internet-exposed assets, a process that is called EASM (external attack surface management).
ASM provides real-time attack surface analysis and vulnerability management to prevent security control failures, reducing the risk of data breaches. The purpose is to find high-risk assets and check for possible attack vectors, including misconfigurations, encryption issues, unpatched/unknown/outdated software, weak passwords, and the like.
Types of Attack Surfaces
ASM encompasses the following: secure/insecure assets, known/unknown assets, shadow IT, active/inactive assets, managed/unmanaged devices, software and hardware, IoT devices, cloud assets and resources, SaaS, and vendor-managed assets.
It has several specialized categories under its purview, and each focus on specific kinds of assets and their related attack surfaces. The types of ASM attack surfaces include:
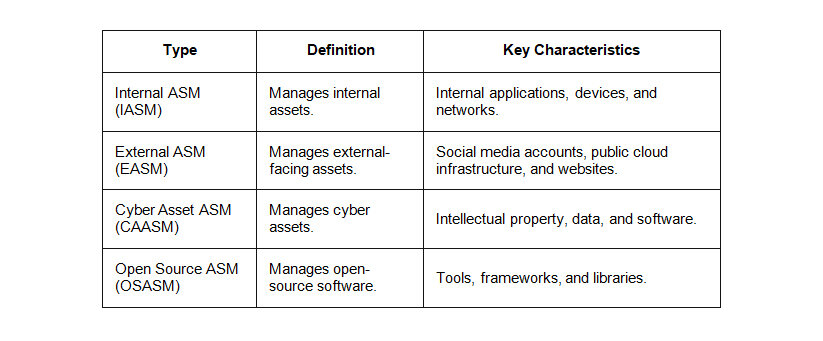
- Known/unknown assets: Known digital assets are applications, systems, and devices that an enterprise’s security teams know of and have authorized to connect to the network. Security teams are unaware of unknown assets and have not authorized them to connect to the network. These could include ransomware, unauthorized devices, and shadow IT.
- Rogue assets: These are known digital assets connected to a network without authorization. They could be challenging to manage and detect as they are not included in an enterprise’s security controls or inventory.
- Vendors: These could be cloud service providers, software vendors and other third-party service vendors, who could risk enterprise security by introducing weaknesses/vulnerabilities in the data or network. Management could range from contractual security requirements to regular security assessments and ongoing monitoring.

How ASM works to defeat attackers
ASM identifies all the assets connected to an enterprise’s IT infrastructure. After analysing how they are interconnected, it determines if those connections provide entry points that can be exploited by hackers to gain access to the network. It then deploys mitigations to protect vulnerable connections and assets. The four key processes are:
- Discovering assets: ASM creates an asset inventory for the security team by scanning for and identifying internet-facing cloud assets, software, and hardware that could act as possible entry points for hackers wanting to attack an organization.
- Prioritising assets: ASM then prioritises the assets based on the likelihood of hackers targeting them, any possible potential impact if they were compromised, and whether this could compromise other assets.
- Remediation: The results of the previous task direct the process of remediation. It includes not only applying missing security controls such as stronger encryption, patches, or updates but also removing orphaned/rogue assets, applying security policies to assets previously unknown, and ensuring that third-party/subsidiary assets meet the enterprise’s cybersecurity policies and standards.
- Monitoring: Finally, ASM monitors, detects, and assesses newer attack vectors and security vulnerabilities in real-time so that it can alert security teams if necessary.
Since modern IT environments are constantly changing, ASM tries to visualize all these processes as much as possible to enable them to run continuously. Thus, security teams are always assured of an up-to-date and complete inventory of exposed assets.

Why ASM is critical
Cybersecurity strategies have always focused on protecting, classifying, and identifying digital assets. ASM automates these activities, covering assets outside the scope of traditional endpoint protection controls, firewalls, and mapping. It continuously maps the attack surface and realigns security thinking from the defender’s point of view to that of an attacker. Hence, security teams are better equipped to prioritize attack surface areas and can move quicker than hackers when vulnerabilities are exposed.
With the cybersecurity landscape changing and evolving at an unimaginable pace, the enterprise attack surface is also changing continuously. It is due to its complex nature and map that attack surface management is becoming all the more critical and will continue to be important in the coming years.
In case you missed:
- AI-Red Teaming: How Emulating Attacks Help Cybersecurity
- Enterprise Network Transformation: Benefits and Challenges
- Improving Enterprise Network Connectivity In The Digitization Age
- Re-examining Cybersecurity through Blockchain
- Cryptography in Network Security – Concepts and Practices
- Top cloud migration myths
- Tackling The Most Critical Cloud Security Vulnerabilities
- AI Firewalls and How They Protect Your Data
- Everything you need to know about Digital Asset Management
- The Best Multi-Cloud Identity Management Practices