Cloud computing may conjure up images of breezy unreal things but it is very real and is changing the world as we speak. Uma finds out how
Ever wondered where the information you key into the digital space is stored? Where does it ultimately reside? Or how safe is it? And how it is ensured that it does not get into the hands of people who can misuse or manipulate it?
The traditional definition of anything to do with ‘cloud’ may lead to ideas of ‘wooliness’, ‘lost in reverie’ and other notions of intangibility. What started as a non-starter, is now a go-to for everything in technology.
It is soon becoming one of the most credible forms of managing computing resources. There were lots of questions around service availability, privacy, and trust in comparison to on-premises storage. But how does work ‘trust’ some systems and services that you cannot ‘physically’ see or quantify?
Many of us implicitly trust our service providers to do the ‘due-diligence’ before we hand over our personal data. The most regulated of them are financial services organisations, which some of them have not adopted technologies that are not fully proven yet.
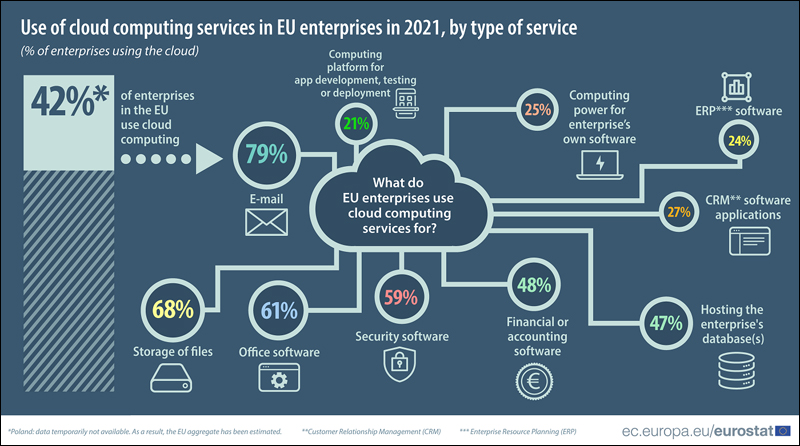
Clouded definitions:
There are various terms emerging when it comes to technology provisioning that are not ‘physically’ made available within the businesses. Businesses take a decision to use technologies to reduce physical burden of maintenance or enhance scalability or just use a ‘pay as you go’ option for ease.
While ‘cloud storage’ merely manages data storage on the internet and making it accessible, ‘cloud computing’ extends running the entire processes and software over the internet.
Some of the examples of storage are Google Drive, drop box, iCloud while cloud computing extends to virtual desktop hosting, application hosting, website hosting, ecommerce and the list is endless.
“Earlier in the 2000’s we used to do remote-desktop login, from remote locations to work on my Personal computer at office, now I can log-in from anywhere in the world thanks to Desktop Virtualisation and application hosting. During COVID times, my infrastructure team was seamlessly able to expand and provision to our 5000+ staff to log in from their personal laptops, safely and securely at the same time. We normally used to have work from home staff ranging to about 20% of our staff at any time before the pandemic! This option was unheard of 20 years ago!” Madhav Gulati, an IT professional explains.
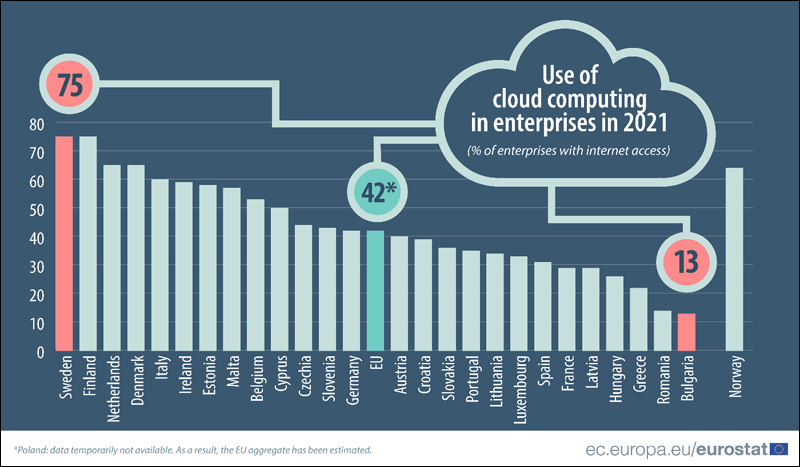
Software developers who were struggling with physical storage extensions for the stress testing or performance testing, now can expand their systems at the press of a button using Software as a Service (Saas).
Amazon Webservices, Azure and Google have expanded the market where Infrastructure, Software, Platforms, now there are brand new terms being provided as a part of Cloud computing services.
Trusting Cloud Technologies:
Trust in general is broken in the computing world as Credibility Trust and Decision Trust. It is subjective based on the welfare and feeling of security despite negative consequences. There are many models that are being built to manage a ‘Trust Model’ to objectively work through the Cloud computing and storage requirements in an organisation.
A Trust model measures the security strength and computes a trust value. It employs various parameters and dimensions that measures the security of clous services. CSA (Cloud Service Alliance) assess security and validity of the service and models. These range from Reputation based trust, Service Level Agreement based trust and various transparency metrics. The most quantifiable one of them is the SLA verification. Some organisations without technical capability also employ trust brokers.
To increase cloud transparency CSA launched the Security, Trust and Assurance Registry (STAR) programme, which is a free publicly accessible registry which allows cloud providers to publish their self-assessment of their security controls in a prescribed format using assessment questionnaires, or controls matrix which utilise the published practices. Various examples can be found of self -assessments can be found at the CSA STAR Website. While these are self-assessments, there are independent third-party professional organisations that can be employed to gain further assurance as well.
While trust can be established based on the assessments, continued transparency on the service provisions on configuration, vulnerability, audit, service statistics require evidence-based confidence so that what is claimed is indeed happening.
There is a Cloud Trust Authority (CTA), which provides a single point for configuring and managing security of cloud services from multiple providers to provide visibility and control coupled with formal audits, accreditation, and standards.
What’s next?
While Cloud computing is here to stay, there is a newer concept emerging called as ‘Edge computing, where the data processed is computed in distributed device notes. Additionally, there are specialised clouds designed for limited audience with known demographic characteristics to perform specific activities. There are also interactive clouds, to enhance transactional computational capabilities for large volumes of data within seconds.
Cloud technology is growing at a rapid rate and will make the future of computing only brighter!
In case you missed:
- None Found










1 Comment
Thank you for sharing the information about the up in the cloud, it is good article, keep sharing .