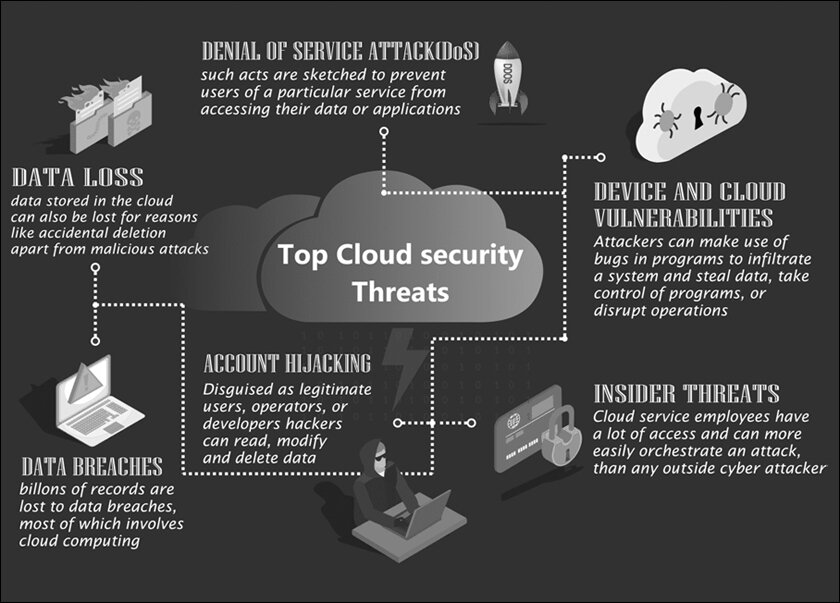
The gaps or weaknesses in cloud computing environments allow hackers to exploit and disrupt services and steal data by gaining unauthorised access.
It’s a given now that if there’s anyone who’s somebody in the internet infrastructure arena isn’t moving to the cloud, then they’re falling behind. Thus, cloud security has been featured on important trend lists for the last few years, showing no signs of abating. In fact, CrowdStrike’s 2023 Global Threat Report identified the “continued rise of cloud exploitation” as one of the major themes. Even Palo Alto Networks listed several cloud security blind spots to watch out for. Clearly, cloud migration and transformation are on everyone’s agenda – and so should cloud vulnerabilities. These gaps or weaknesses in cloud computing environments allow hackers to exploit and disrupt services and steal data by gaining unauthorised access. While cloud security threats are well-known, the point is to be able to tackle them. Here’s a lowdown on how to tackle the most critical cloud security vulnerabilities.
Poor Identity Access Management
Since digital identities now outnumber human identities, poor access management leaves cloud environments vulnerable. Identity is now the new frontier of cloud security. However, Identity Access Management (IAM) is notoriously complex and is responsible for almost 61% of analysed breaches in a 2021 Data Breach Investigations Report by Verizon.
That said, there are some basic steps an organisation can take to mitigate IAM threats. These include using a cloud access security broker (CASB) to monitor and control cloud resource access. When it comes to educating employees, conducting training sessions outlining proper access management practices is essential. On the permissions end of the spectrum, organisations must adopt single sign-on and multi-factor authentication solutions, thus granting the “least privilege” access to cloud resources. Furthermore, they should also employ an RBAC (role-based access control) to grant users only the required permissions to complete tasks.
All these steps are also a part of the best multi-cloud identity management practices.

Data Leaks from Misconfigurations
The National Security Agency (NSA) called cloud misconfigurations the most threatening to cloud security in 2020, and it’s still true. These are errors in the security settings of cloud systems and applications, including IaC (infrastructure as code), serverless environments, containers, and virtual machines. They usually occur due to security misconceptions, lack of awareness, and administrative oversights, causing severe data breaches.
One of the top measures for keeping misconfigurations at bay is using a CSPM (cloud security posture management) tool to rectify cloud configurations and conduct regular audits. Implementing least-privilege access to resources is a given, but what’s really needed is implementing IaC for maintaining correct and consistent configurations.
Rogue APIs
The future is and will be driven by APIs (Application Programming Interface). These applications allow software programs to communicate with each other, including unrelated external services. Now, the problem with weaknesses in APIs is the same as that of misconfigurations – exposing sensitive data and data breaches. When a vulnerability arises in APIs, leaving them unpatched could give hackers a free pass into any system, allowing them to gain admin access by bypassing authentication and stealing company secrets.
Take the Twitter (now X) December 2021 API breach, for instance. During the incident, attackers were able to access the data of more than 5.4 million Twitter users by exploiting a particular vulnerability in the Twitter API. It allowed them to submit phone numbers or email addresses to the Twitter API to retrieve associated Twitter accounts.
The way to tackle rogue APIs is four-fold. One is to scan APIs for vulnerabilities regularly by monitoring and auditing API activity. The second way is to implement strong authorisation and authentication mechanisms for cloud APIs. Next, organisations need to use encryption to transmit data. Last but not least, they need to employ rate limiting and a bevvy of other controls to prevent abuse of APIs.

Lack of visibility
Enterprises mixing and matching cloud technologies from different providers (multi-cloud environments) leads to a highly complex and constantly evolving dynamic environment. So, it makes it very hard to get a full picture of and complete visibility into security issues, allowing cloud security vulnerabilities of different proportions to go unnoticed and undetected.
This might seem like an extension of IAM, but it needs to be addressed as a discrete cloud vulnerability. And it’s impossible to assess cloud vulnerabilities without having a context-based, centralised visibility of the entire ecosystem. It’s also possible for such vulnerabilities to go undetected for years. For instance, Toyota Japan unknowingly exposed the vehicle and personal data of over 2 million customers for almost a decade.
The way out of this quagmire is, again, four-fold. The first thing enterprises need to do is employ and implement a cloud-native application protection platform (CNAPP) solution. It’s an all-in-one cloud-native software platform that ensures visibility into all cloud activity and assets by streamlining the monitoring, detection, and action of cloud security vulnerabilities. The next thing to do is ensure centralised monitoring and logging solutions for all cloud resources. Lastly, enterprises must set up alerts for unauthorised/unusual activities and regularly review and prune unnecessary resources.
In case you missed:
- All About Attack Surface Management
- Edera: An All-Women Startup Revolutionising Cloud And AI Infrastructure Security
- Re-examining Cybersecurity through Blockchain
- Six ways hosted private cloud adds value to enterprise business
- Top cloud migration myths
- Password Practices For A Safe Digital Presence
- AI-Red Teaming: How Emulating Attacks Help Cybersecurity
- Improving Enterprise Network Connectivity In The Digitization Age
- Cryptography in Network Security – Concepts and Practices
- Enterprise Network Transformation: Benefits and Challenges









