Author: Deborah Jasmine Gabriel
Deborah Jasmine Gabriel is a technical writer and content strategist with over 12 years of experience in global scientific and academic publishing, consulting and professional services firms, and the cybersecurity industry. Her expertise lies in translating complex technical concepts into engaging and accessible content for diverse audiences. Driven by curiosity and a passion for staying ahead of the curve, she creates compelling content across formats like technical manuals, white papers, thought-leadership articles, and social media and blog posts. Deborah brings a unique blend of technical expertise and exceptional writing skills to every project she undertakes. With her versatility, attention to detail, and commitment to continuous learning, she is a trusted partner for organizations seeking to communicate their technological innovations effectively and with impact.
By understanding potential changes around AI, you can strategically position yourself for future opportunities and remain a valuable asset in an AI-driven work environment.Keep reading… Artificial Intelligence has become integral to almost all industries known to humankind. This transforms our roles, capabilities, and responsibilities at work. While AI has the potential to displace specific roles, it also, by all means, creates new job categories in AI development, data analysis, and AI system maintenance. Learn the Art of Adapting and Continuous Learning Watch for emerging AI tools and trends. You can keep yourself plugged in by following industry news, attending webinars,…
Technology plays a very important role in our lives, and it is essential to know its environmental impact… You must include sustainable practices in IT to reduce its environmental footprint. If you choose to adopt eco-friendly approaches, your business will contribute to a healthier planet while still benefiting from technological advancements. Below, we will be covering how energy consumption and managing electronic waste responsibly can help smooth IT operations with sustainability goals. Read more to explore seven sustainable practices to reduce IT’s environmental impact. Energy-Efficient Hardware It is an important aspect of green computing to acquire computer hardware that uses…
To protect against these attacks, organizations must take a proactive approach to managing third-party risk by implementing thorough vetting processes, monitoring continuously, segmenting access, and planning for incidents. Third-party risk management is important due to situations such as the supply chain attacks where firms in different industries face attacks on their vulnerabilities and threats from trusted vendors or suppliers. Companies have to turn to third-party vendors for applications, infrastructures, and solutions; therefore, their attack surface increases. This paves the way for cybercriminals to penetrate even the most secure networks, thereby increasing vulnerability. Now let’s analyze the specifics of supply chain…
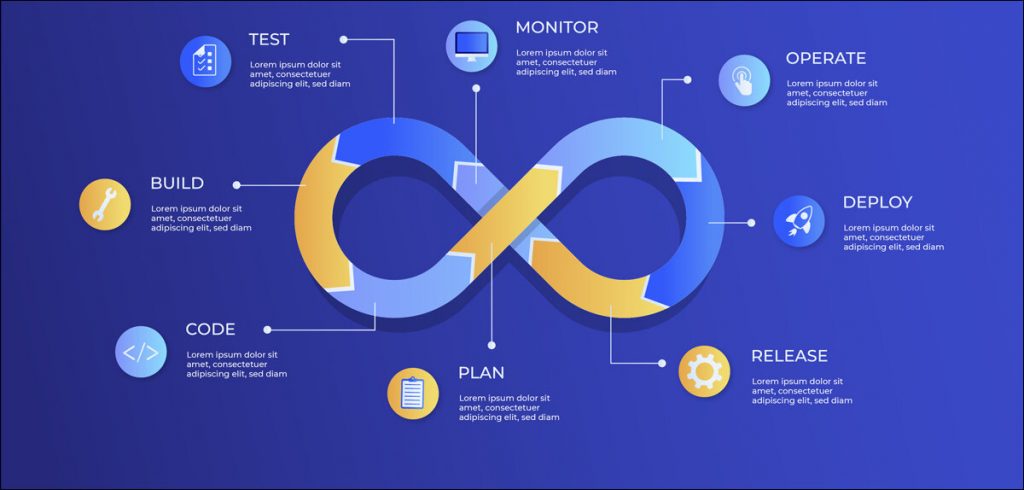
Implement strategies such as automated scanning, secure secrets management, and regular training. The prediction that the DevOps market size would grow exponentially from $10.56 billion in 2023 to $12.8 billion in 2024 at a compound annual growth rate (CAGR) of 21.2% drives home the importance of securing the DevOps pipelines. These pipelines optimize the software development and deployment processes. However, they also introduce new security risks; which is why securing these pipelines becomes so important. This is to identify the vulnerabilities at an early stage. Image Credit: Exigence Blog What Are DevOps Pipelines? DevOps pipelines automate the development, testing, and…
Multi-factor authentication (MFA) protects your online accounts and sensitive information. It adds an extra layer of security beyond just using a password. Want to know how? Multi-factor authentication (MFA) protects your online accounts and sensitive information. It adds an extra layer of security beyond just using a password. Want to know how? Here’s a guide to follow to implement MFA effectively for enhanced security. What do we mean by multi-factor authentication? On implementing multi-factor authentication, you are required to provide two or more verification factors to access any account. If you think MFA uses just a string of passwords, you…
AI initiatives will be successful in the long term only if they are led by human expertise. There is a giant leap from the pre-AI era of manual operations to the post-AI era of automation and innovation. Artificial intelligence is seeing widespread integration into every aspect of business operations. Some of the most trending aspects of AI are Generative AI, Natural Language Processing (NLP), Data Science, and Machine Learning. These models simplify complex tasks and help businesses lay a rock-solid foundation in strategic development. Image Credit: eBiz Solutions The Six Stages of AI Development It’s fascinating to know that AI…
Ignorance is not bliss when we talk about AI. Caution is crucial! AI is reaching the sophistication levels we read and watched in fiction pieces a decade ago. It is becoming more than a transformative development tool, touching every existing industry and every possible use case under the sun. But the rise of deep fakes, viral videos of AI chatbots interacting with each other, misuse of voice cloning technologies, and—the scariest part—AI evolving to the extent that it goes beyond human control raise the alarm for ethics in AI. Ignorance is not bliss when we talk about AI. Caution is…
Know the essential tips to safeguard your business from ransomware threats and secure valuable data effectively. Ransomware is considered to be one of the formidable threats to cybersecurity. This is a type of malware that attacks computer systems and locks data, making its access possible only after the payment of the demanded ransom. In addition to monetary loss, organizations also face reputation and operational loss. There are primarily two types of ransomware: locker ransomware that locks the victim out of the system and makes it impossible to launch the operating system, applications, and files. The other type is crypto ransomware.…
Read about zero trust security and how it paves the way for enhanced security. With the advent of cyber criminals who are mastering their craft continuously, the security of digital resources is one of the main issues that concern people and companies. Zero Trust Security is a security concept that starts with the assumption that nothing, both inside and outside the company or organizational networks, should be trusted. However, organizations have to ensure and authenticate anything that is attempting to connect in their systems before it can be allowed to connect. This model considers some of the current issues of…
Learn how data residency regulations impact businesses and ensure compliance with laws. Data residency is the set of laws, policies, and regulations applied to the data collected and processed by businesses. It requires that the data be stored on physical or virtual servers located within certain geographical boundaries. Data residency laws exist in order to protect personal data, control and allow access, and ensure privacy, by restricting data to the legal territory where there are specific laws on the protection of data. Image Credit: Vecteezy Impact on Businesses Organizations need to either build local data centers or arrange for the…