It’s not just the job of the security team anymore! An important aspect of DevSecOps is a shared sense of responsibility towards security, writes Nigel Pereira
As the focus of the enterprise has shifted towards pushing changes to production as quickly as possible, security is often left on the back burner. In a mad scramble to harness the power of the cloud to remain relevant and competitive, organizations end up leaving huge gaps in security that cannot be addressed as an afterthought. These gaps could be caused by anything from a misconfiguration to an insecure service being enabled or even a vulnerability inherited from an open-source component like in the case of the Equifax breach that cost over $1.7 billion.
The modern security dilemma
It’s easy to think of security a detail to fill in at a later date because that’s how it has always been done. In fact, the internet itself was secured as an afterthought to quote internet pioneer Dan Lynch who said “When we were first starting to test the first internet, we looked at security and thought that it would be too difficult to include at this phase.” He then adds “bad choice, eh? We never looked back until it was too late.” What he means by too late here is the fact that the internet we use today is still inherently insecure!
Yes, that’s right, the digital network that we use for literally everything was not designed with security in mind and is officially deemed “insecure.” To add to that, modern cloud-based environments typically span multiple public clouds, private clouds, and on-premise resources.
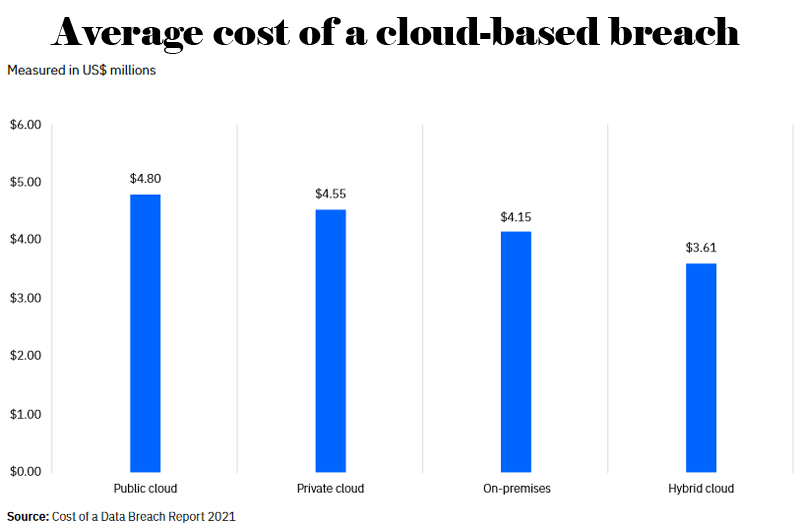
These hybrid environments are hard to secure using traditional perimeter security measures because the perimeter or “attack surface” is too large and constantly expanding. Additionally, every time you add a new cloud-based application or open-source tool, you’re effectively increasing your attack surface exponentially.
The problem with DevOps

DevOps is about optimizing for development speed with the security aspect added at the end of the development pipeline. While this approach used to work well when networks and perimeters were well defined and could be placed behind a firewall, a lot has changed since then. In addition to complexities associated with securing hybrid environments, the pandemic has caused a major shift regarding where work is done. This has in turn caused the so-called “perimeter” to shift to anywhere an employee decides to log in with their laptop or smartphone. We’re talking about an ethereal, shape-shifting boundary that requires re-thinking of fundamentals to properly secure.

While DevOps was meant to break down Silos, it’s still pretty “Siloed” if you’re to build your entire application and then chuck it over the wall at your security team. DevSecOps, on the other hand, is all about having your security team on board from day one, getting their feedback at every step, and integrating automated security tests across the pipeline as much as possible. Another important aspect of DevSecOps is a shared sense of responsibility towards security and how it’s not just the job of the security team anymore.
Secure coding practices
As opposed to application and infrastructure being the sole responsibility of the security team, DevSecOps makes security a joint obligation. With regards to development teams, in particular, this involves secure coding practices to ensure applications are inherently protected from the ground up. OWASP provides a useful checklist of secure coding practices that include 14 areas of consideration. The first and the most important item on the list labelled “security by design” is all about optimizing for security as opposed to development speed. Other Secure coding practices include using version control systems like GitHub to keep track of changes and AppSec tools to automatically identify known vulnerabilities in third-party tools.
While DevSecOps may slow down development in the short term, it’s the wiser choice when you consider what’s at stake. Cybercriminals are growing exponentially in sophistication by leveraging technologies like AI and Machine Learning and the cost of cybercrime damages is expected to reach $8 trillion by the end of 2022. That’s what’s at stake here, and while security teams need to work endlessly toward securing an ever-expanding perimeter, a hacker attacks every 39 seconds and requires just a single successful breach to cause untold damage.
Don’t trust anyone
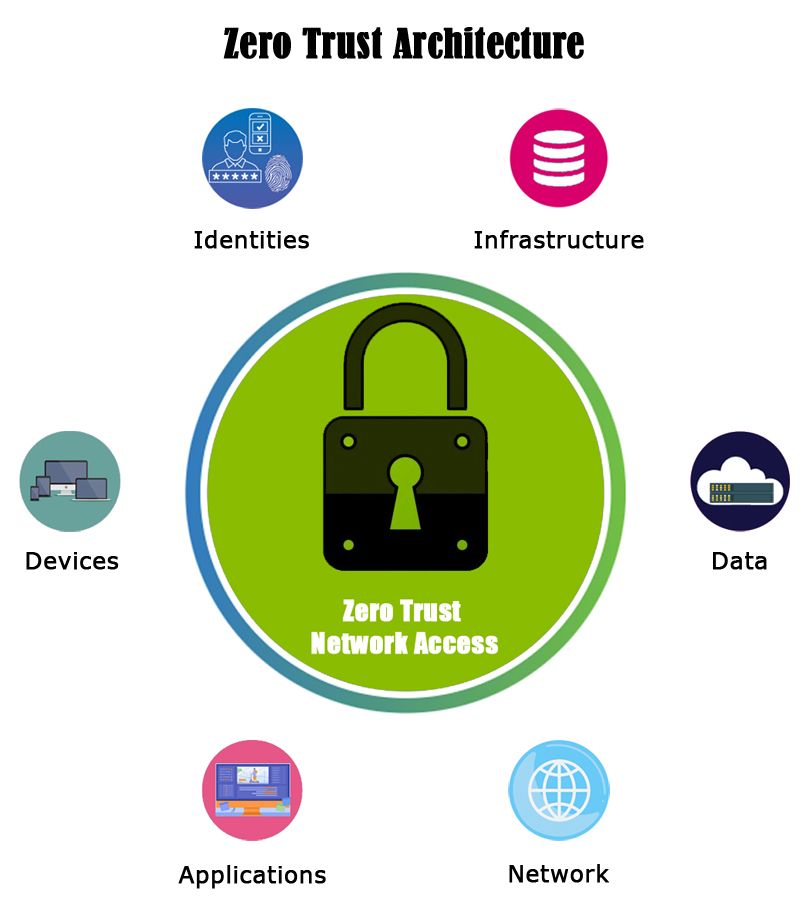
With the internet being inherently insecure and traditional methods of perimeter security turning obsolete, an idea that seems to be catching on is a security framework called Zero-Trust. With traditional methods of perimeter security turning obsolete, an idea that seems to be catching on is a security framework called Zero-Trust. While traditional software is built on a conception of implicit trust, this one is developed with no trusted perimeter, and every connection is suspicious until proven otherwise. This is a fundamental change in the way we look at a network since it has more to do with network policies than an actual physical network.
In conclusion, if you want the reason for DevSecOps in a nutshell, Applied Risk founder and CEO Jalal Bouhdada was quoted stating “despite increased awareness, new technologies are still regularly developed and deployed in a way that prioritizes speed to market and costs over key security considerations.”
In case you missed:
- Will Pi Coin Be the Next Bitcoin? A quick Reality Check!
- Netflix replaces its game developers with AI
- A Glowing Plant Could Be Your New Night Lamp for $29
- So AI can get bored, “suffer,” and even commit suicide?
- CES 2025: NVIDIA’s Cosmos Just Gave Robots a ‘ChatGPT Moment’!
- Having two left thumbs may no longer be a bad thing
- CDs are making a comeback, on a petabyte-scale capacity!
- Scientists establish two-way Lucid Dream communication!
- This computer uses human brain cells and runs on Dopamine!
- Researchers develop solar cells to charge phones through their screens










2 Comments
Thank you for the good writeup. It in fact was a amusement account it.
Look advanced to more added agreeable from you!
By the way, how could we communicate?
Thank you for sharing the information about devsecops is security can no longer be an afterthought, it is nice article, keep sharing.