Never trust, always verify. That’s the keystone to “Zero Trust,” a concept coined long before buzzwords like ML (machine learning) and AI (artificial intelligence) dominated the world of cybersecurity.
Zero Trust is exactly what it sounds like – a security model based on the principle of not trusting anybody by default, including the ones already within the network perimeter, and maintaining strict access controls.
Research and advisory firm Forrester’s analyst, and now one of the world’s foremost cybersecurity experts, John Kindervag coined the name Zero Trust in 2009. The objective? To have security teams eliminate the risky trust assumptions that were resulting in devastating data breaches. Since then, security vendors have hijacked the term, eager to milk the advantages of the hype surrounding the concept.
It’s so misused and overused today that it feels like a meaningless buzzword — however, that’s far from the truth. In fact, the very fact that countlessvendors have tried and capitalized on it showcases its power and potency. Imitation is the sincerest form of flattery, indeed. This article delves into what makes zero trust “zero trust” and why it’s becoming increasingly popular in a world with increasingly sophisticated cyber threats.
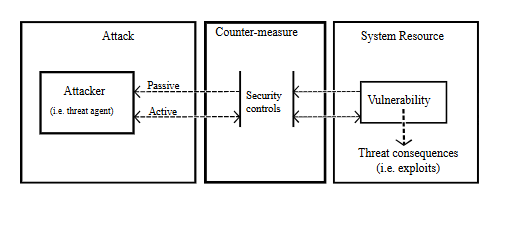
What is zero trust?
Zero trust is a cybersecurity strategy/model in which no individual/computing entity is considered inherently trustworthy, notwithstanding whether they’re outside or within the enterprise network. It’s different from the former traditional way of thinking that every individual/device on a corporate network, i.e. on the right side of a firewall, was allowed access to resources and data. The issue with this is that once hackers gain access to the network, they’d have free rein over everything on the inside.
Broadly speaking, users in enterprises with zero trust security need to be authorized and authenticated whether they’re within the corporate headquarters or logging on from a public Wi-Fi network outside. The principle is simple: least privilege. So, data and systems are locked by default, with access being granted only to the extent that’s required to meet specific goals.
This ensures that attackers who’ve managed to slip past the enterprise security can’t access restricted functions or data. Furthermore, this “lack of trust” works both ways: Users should be able to authenticate the applications as well using signed digital certificates or something similar, ensuring that they don’t accidentally activate or encounter malware.
How Does Zero Trust Work In An Organisation?
ZTNA (Zero Trust Network Access) is the main technology that makes it possible for enterprises to implement a zero-trust security model. ZTNA is similar to an SDP (software-defined perimeter) approach when it comes to controlling access, concealing most services and infrastructures on the devices connected to the network. So, these devices aren’t aware of any resources (servers, applications, etc.) on the network besides what they’re connected to.
For instance, if every resident of a city were to get a phone book with the phone numbers of every other individual in the city. So, anybody could contact every other person. However, if everyone were to have unlisted phone numbers, one would have to know another specific resident’s phone number to get in touch with them. In the second scenario, there are no accidental calls to the wrong person, no unwanted calls, and, best of all, no chances of spam or fraud.
That’s the entire basis of ZTNA, which employs “unlisted” services, applications, and IP addresses. It sets up a one-to-one connection between a user and the resource they need, not giving the user access to anything more than what they require to complete their task.
Furthermore, all of ZTNA’s connections need to be recreated and re-verified from time to time.

How Is Zero Trust Different From VPNs?
Incidentally, there’s one venerated security technology that doesn’t feature on the list of potential zero-trust elements, and that is VPNs (virtual private networks). In a world before zero trust, VPNs offered secure connections between corporate networks and devices outside those networks, thus allowing them access to internal resources.
Zero trust looks beyond being “outside” or “inside” secure networks, replacing VPNs with an array of granular tools for authorizing and authenticating users. The idea is to assess potential threat postures of devices based on a wide array of signals, and the user’s network location is just a single aspect.
Marching Ahead
The zero trust architecture and setup has been in vogue for decades. However, the push to adopt it now is happening because of three aspects. The first is cloud adoption in most organisations to speed up and improve their digital transformation adoption. The second is within-organisation attacks, which emanate and move inside an organisation and compromise its assets.
Finally, it’s attacks that rise within the organisation, but compromise assets outside its IT landscape. Heading into 2025, the conversation is no longer about whether the zero-trust model is necessary – it’s about what can be possibly done to further its adoption and make enterprise security stronger and impenetrable. With Gartner predicting that 60% of enterprises will embrace “Zero Trust” as a starting point for security in 2025, it’s no surprise that zero trust is poised to fundamentally shift how we view the cybersecurity ideology.
In case you missed:
- Enterprise Network Transformation: Benefits and Challenges
- Improving Enterprise Network Connectivity In The Digitization Age
- Re-examining Cybersecurity through Blockchain
- Cryptography in Network Security – Concepts and Practices
- All About Attack Surface Management
- Top cloud migration myths
- Multiplexing in Networking: An Overview
- Edera: An All-Women Startup Revolutionising Cloud And AI Infrastructure Security
- Colocation Data Centres: An Overview
- Star Topology – Benefits and Challenges