Read about zero trust security and how it paves the way for enhanced security.
With the advent of cyber criminals who are mastering their craft continuously, the security of digital resources is one of the main issues that concern people and companies.
Zero Trust Security is a security concept that starts with the assumption that nothing, both inside and outside the company or organizational networks, should be trusted. However, organizations have to ensure and authenticate anything that is attempting to connect in their systems before it can be allowed to connect. This model considers some of the current issues of security where threats can be local or remote and the idea of an internal trusted network is outdated. Zero Trust principles require users and devices to be authenticated and authorized before they can access an application or data.
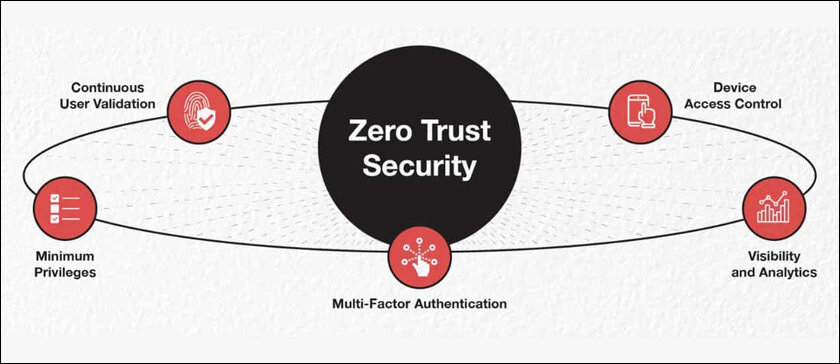
Principles of Zero Trust Security
Verify Explicitly – Authentication and authorization are based on the following factors: user identity, location, device health, service or workload, data type, and data irregularities.
Use Least Privilege Access – Grant users and devices the necessary level of access to perform their functions. This reduces the likelihood of attacks from malware or hacking.
Assume Breach – Assume there are already attackers in the network environment when performing an assessment. This includes increasing surveillance and adopting sophisticated threat detection techniques in order to respond to threats quickly.
Implementing Zero Trust requires a complete overhaul of the IT architecture. This architecture incorporates enhanced security mechanisms and approaches to achieve a high level of access control. Components include identity and access management (IAM), microsegmentation, and encryption. The architecture also tries to partition segments within the network isolating critical IT assets and applications to ensure that any threat which gets in is contained, preventing any further lateral movement.

Zero Trust Technologies
Multi-factor Authentication (MFA) prevents brute-force attacks where an intruder can log into an organization’s system just by using valid user credentials. The identity must be verified in different ways, including more than one form of identification, while Identity and Access Management (IAM) maintains digital identities and user privileges, as stricter verification of the identities is needed.
Encryption protects data at rest and in transit, making it impossible for unauthorized intruders to access the information on the network, and endpoint security involves a set of features at the device level to secure points of access to the network
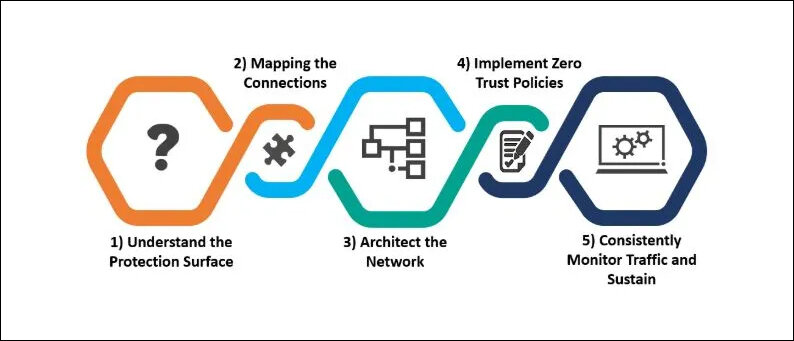
Zero Trust Best Practices
Continuous monitoring and response proactively employ tools that search for unusual activity and deploy measures to counter identified risks; educating and training employees ensure employees undergo training on security and operational practices frequently.
Regularly updating and patching systems make sure that all the software and systems are updated to protect against all possible weaknesses and vulnerabilities, while segregating and enforcing network segmentation subdivide the networks and prevent attackers from accessing the entire network and inspect traffic between segments to limit attackers’ movements.
Business Use Cases of Zero Trust Security
Banks and other financial organizations have incorporated Zero Trust solutions for securing crucial financial data and client data. In these institutions, every access request is validated, regardless of the source of the request; this can effectively prevent any breaches and data access by unauthorized persons, which is very important.
Zero Trust is used by hospitals and other healthcare facilities to protect patient details and ensure that their records are easily retrievable yet secure. The concepts of microsegmentation and proper access control guarantee that the medical personnel will have access to only the proper data that is relevant to perform their duties, thus eliminating the problem of data leakage.
The primary goals of government agencies are to protect from external threats and individuals who try to abuse their privileges by controlling the access to networks and data while closely monitoring the network and data interactions.
Adopting a Zero Trust framework reduces the risks associated with data breaches and unauthorized access. Organizations can protect their digital assets more comprehensively by verifying every user and device, limiting access on a need-to-know basis, and implementing strong encryption and analytics. Transitioning to Zero Trust might require a considerable initial investment in time and resources, but the payoff in enhanced security is invaluable.
In case you missed:
- None Found










