Embark on your digital transformation journey with confidence by learning about the top cybersecurity pitfalls to avoid.
The term digital transformation is often used to describe businesses that aim to introduce changes to their business models. Such change is important but has a negative impact on organizations in terms of multiple cybersecurity risks. When firms become digital, they gain many opportunities but these also provide additional avenues for cyber fraudsters to exploit.

The following blog post presents an overview of the top cybersecurity pitfalls so that you are aware about how best to safeguard your data and defend your organization during your digitization process.
Cybersecurity in digital transformation refers to the ability to ensure the continuity of business activities in the event of potential cyber threats and the use of mechanisms to protect the privacy of information and the trust of customers. A lack of effective cybersecurity measures causes significant financial setbacks and legal penalties and destroys the image of the company.
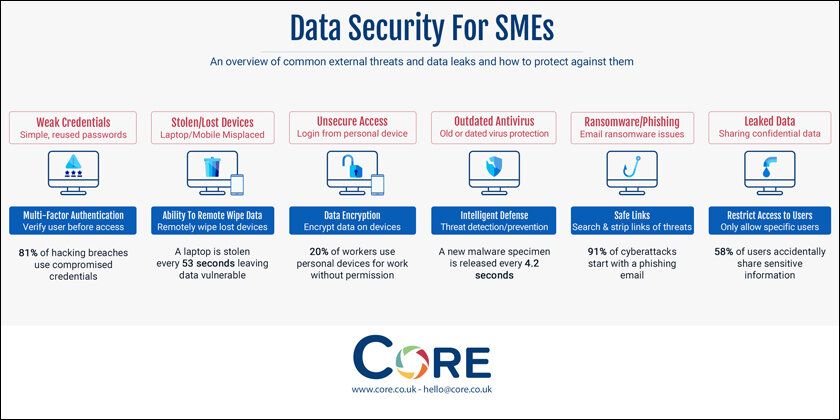
Common Cybersecurity Pitfalls to Avoid During Digital Transformation
Lack of employee cybersecurity awareness
One of the biggest vulnerabilities as far as data security is concerned is the employee, as a single mistake is bound to lead to massive data breaches. Teaching employees how to recognize phishing, hacking, and social engineering attacks is crucial. That is why ensuring that all workers in the company are aware of the various cyber risks is the most important way to protect the company from cyber threats.
Neglecting regular software updates
Another major threat is the failure to regularly update systems. It is crucial to update and patch software to eliminate possible security threats.
Insufficient data encryption measures
Another serious risk that could emerge during digital transformation is that of insufficient data encryption. Companies need to secure data in transit and those stored in databases and networks through the use of encryption techniques, including SSL/TLS for websites and communication that employ end-to-end encryption.

Emerging Cyber Threats
Attack surfaces keep expanding, new vulnerabilities keep emerging, and the impact of potential security breaches keeps worsening.
1. Social engineering
Social engineering involves manipulation; attackers apply human psychology to control victims to carry out desired actions. Phishing emails or pretexting commonly entail precisely scripted emails or situations to deceive people to provide information or gain entry to restricted components of an organization’s digital infrastructure. The prevalence of the work from home arrangement has further made it easier for such tactics to be implemented since most of the employees are not working from a secure office environment.
2. Ransomware
Ransomware is a malicious software that takes an organization’s data hostage and requires money to be paid in exchange for it to be unlocked. Hackers target digital transformation initiatives; these attacks can have a devastating impact on operations and result in significant financial losses.

Data Protection and Threat Prevention with the Help of Technology
Real-time threat detection (RTTD)
RTTD solutions are very crucial in detecting cyber threats and eliminating them before they cause harm to an organization. These technologies continuously analyze network traffic, system logs, and users’ behavior using sophisticated behavioral profiling techniques to detect anomalies that may or may not indicate potential security threats. Early detection is also paramount since organizations can react to threats as soon as possible, and this may help to eliminate or prevent negative events.
Artificial Intelligence (AI)
The ability to learn continuously enables AI to respond to new threats as they develop, hence providing a reactive defense system. AI is changing the way we address cybersecurity, offering capabilities way beyond human capabilities. AI systems can process terabytes of data in seconds to predict cyberattacks. AI is also capable of carrying out repetitive cybersecurity functions to help analysts deal with complex threats. The vast potential of AI allows organizations to predict and prevent attacks before they take place and move from the defensive attitude to the offensive one.

Cybersecurity Best Practices
1. Multi-factor authentication (MFA)
MFA is an access control system that ensures that users provide two or more authentication conditions to access a system or an application. It ensures that if a password is leaked or compromised, then there is still another layer of security.
2. Regular vulnerability assessments
Vulnerability scanning is essential and should be conducted at regular intervals to identify potential loopholes and patch them before they are uncovered by the malicious actors. These assessments should be done both on a routine basis and after major changes in an organization’s digital platforms. Early discovery of weaknesses will allow firms to address them before causing damages, thus minimizing the potential window for cyberattacks.
3. Security awareness training to employees
Employees have become the first layer of defense in the face of cyberattacks. They should be well trained on how to identify and manage security breaches, proper internet usage, and password creation rules through mandatory periodic training.

Final Thoughts
The digital transformation journey can become quite dangerous without the proper cybersecurity strategies. These aforementioned risks reveal the importance of ensuring that the security mechanism encompasses not only technological aspects but people and processes as well.
It is clear that the path of digital transformation can be beneficial and full of opportunities; at the same time, it requires a thoughtful and careful approach. Cybersecurity is not a one-off event but a perpetual exercise that is critical to the success of digital transformation initiatives.
In case you missed:
- None Found










